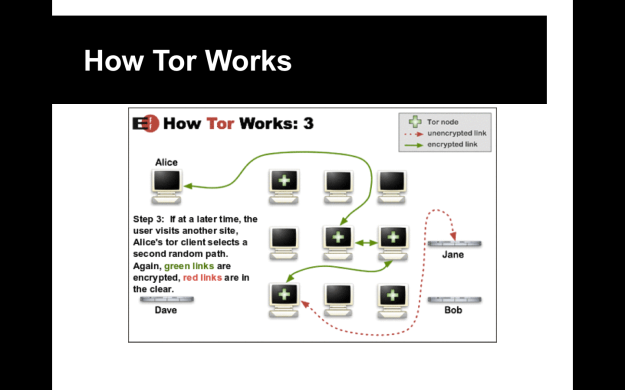
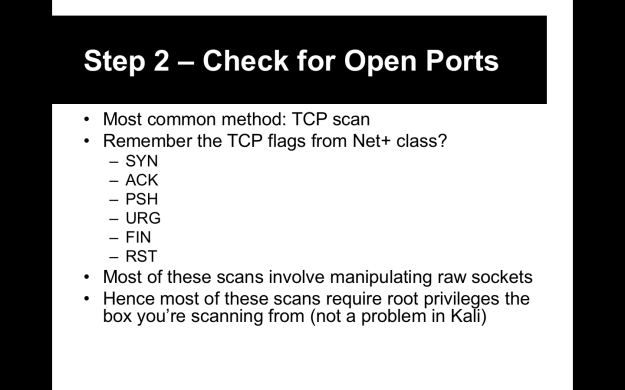
In 2015, I had the good fortune to come upon a part-time gig teaching a course at a local community college in the Louisville, KY area. The course’s goal was to prepare students to sit for the EC-Council Certified Ethical Hacker (CEH) exam. Say what you will about CEH, and EC-Council for that matter, but CEH is a decent introduction to the concepts behind penetration testing. Plus, more and more job listings are asking for it, so it’s one of those all-important HR filter bypasses you can purchase for $500…much like the CISSP. It won’t make you into a penetration tester, but it at least demonstrates that you understand the concepts and can navigate a Linux command-line and use nmap without looking like a moron.
I was able to land in infosec right out of college, joining a consulting firm in Chicago. I’ve done policy work, security architecture, vulnerability remediation, and other tasks, but I always wanted to break into penetration testing. My job at the time allowed me a few opportunities to get in on pentests, but it was far from my primary responsibility. Unfortunately, the Louisville area didn’t have very many pentesting opportunities and breaking in to such an area of expertise is hard. I’d gotten the CEH back in 2010, with my eye on using it as a foot in the door, and had alerts set up on several job sites to inform me of any jobs with keywords like “penetration testing,” “CEH,” or “hacking” in them. That was how the adjunct instructor gig came to my attention.
I say I was fortunate to find it for several reasons. One, I’ve always loved teaching and presenting, and sharing knowledge with some really great students is it’s own reward. Two, it helped reinforce my own knowledge of the field and actually helped me to blow ’em away in the interviews when a penetration testing job opportunity finally did come along. Really, there is no better way to learn a subject, inside and out, than to teach it to others. It forces you to build a deep, comprehensive knowledge of that subject so that you’re prepared to answer any question from your students and clear up any confusion they may have. For example, my own understanding of buffer and heap overflows was pretty shallow until I was forced to explain it to students with almost no background in C programming.
I taught two semesters of this course before landing my current job, which forced me to relocate to Raleigh, NC. Since those PPTX files are just gathering dust, I figured I’d post them here publicly and see if anyone else gets some good out of them.
The original course was at night’s, twice a week for 11 weeks, and each class was about four hours long. I’ll post pics and notes Obviously, I can’t simulate all of the original lab conditions here…but where applicable, I’ll direct you to some online tutorials that’ll show you how you can do it on your own, using VMs or whatever.
The original course was supposed to be based on EC-Council’s official training material (Ethical Hacking & Countermeasures). EC-Council normally requires you attend their sanctioned training or boot camps before they allow you to sit for their exam, otherwise you can apply for a self-study waiver if you have a year or more of experience in information security. By teaching from their books, this was how they allowed students to sit for the exam.
EC-Council’s official training material is mostly garbage, and I don’t say that lightly. Very poorly edited, typos and formatting errors abound, at times an incoherent mess of constantly jumping between topics, and I never saw a screenshot of a system newer than Windows XP. I used the books as a vague outline of what topics I should cover, then wrote all the presentations myself using different resources to fill in the needed information. Overall, I tried to make the training look more like the OSCP, with a big focus on hands-on labs and CTFs, with a big dose of irreverent humor injected into them. These were 4 hour-long classes, after all, so I had to keep the students’ attention!
At the front of each lesson, I’ll include a link to download the original PPTX file. I actually use the Notes section beneath each slide, so make sure you’re reading it in order to get all the info. Maybe someday I’ll come back and film YouTube videos of these in proper lecture format.
I hope you enjoy them and that you or your friends can use them to better understand the world of penetration testing. If you have any questions or comments, please hit me up on Twitter (either by tweet or DM) at @ch1kpee.